
Startup Jedi
We talk to startups and investors, you get the value.
Evaluation of the startup’s technical compliance with the current investment round and its technological Due Diligence is a necessary step before the investor makes a decision whether to finance a project. Usually, he is worried about the quality of information that the team presents, about their technical accomplishments, technical competences, their ability to follow development plans and scale the solution, as well as, included risks.

Startup Jedi
We talk to startups and investors, you get the value.
For the last 6 years, my service company has been developing websites, in the larger meaning — developing the software. We research modern technological possibilities, innovations, existing systems, and we try to figure out how to use them to satisfy client’s needs for the sake of business: to optimize processes, to develop business model, to enter new markets, to search new ways of production and so on. Primarily, we focus on the open-source, in other words, we use technologies in the open code.
After 10 years of personal experience in IT, I have formed specific expertise in working with the service model in projects that we do for clients. In general, I believe that we are not doing projects for the client — it is coworking with the client, as we are also interested in the project’s success. Thanks to this approach, we do not only have a satisfied client but we also create and develop a working system, new knowledge of what and how to do something in a specific situation, so we can use this production method further on.
We worked on many markets and in many different projects: from small to big scale — it is the way our vision and approach were formed. Moreover, my personal entrepreneurial experience allows me to see the process from both sides: from the side of client’s solutions supplier, and from the side of the person, who can understand business results, that this project gives.
To develop an evaluation methodology for technology, I decided to generalize this experience, to look at it in an abstract way, because that was the task — to create a universal and sufficiently simple methodology that would be suitable for evaluating startup technology from any industry. And in this way, we determine the technological maturity of a startup: how consciously, confidently they choose technologies to make a radical change in the industry, change the way of actual “doing”, radically transform business models or the world around.
In this way, we evaluate whether this technology is worn out, whether it’s popular, whether it’s safe, how easy or difficult it will be to implement this technology while scaling the product and business model.
During the evaluation process, the startup tells about their technologies, their maturity and usability, about the researched alternatives and whether the startup received any other expertise and so on. If we see any difficulties, we have to record that during project checks, and we have to explain, that at some point in the future, there may appear potential problems and challenges, that would have to be solved. But, for example, if there is a mature technology, we may have questions beyond the technology framework: are there a market and a working business model, whether the team is able to answer these questions and at which level of competence?
Elizabeth Holmes led Theranos and claimed to have developed a technology that made it possible to get an accurate blood count from just a few drops. She called this technology completely innovative, she didn’t tell anyone about it and stated that her innovation would disrupt the analysis market and make analyzes accessible even to non-specialists. However, in the end, according to Forbes analysts, the company’s value was approximately zero. Numerous investigations began. A lawsuit was filed against Holmes, claiming that Theranos was unable to provide the required level of reliability and quality of the analysis. The company’s advertisement in the lawsuit was called a fraud, all the activities of the startup were claimed to be fraudulent. — Startup Jedi
As in literature and science, there are ways to calculate a certain analogue of the citation index. The principle of obtaining an authoritative opinion also works there: the presence of an authoritative reviewer in a material, publication, discussion in a specialized publication, and so on. In principle, this model can also be applied to technologies. There are open technologies (open source): everyone can see the code, check, validate it and evaluate it. You can see where this code was used and implemented, assess the cases and see if the technology can be scaled safely. Thus, we compare alternatives that are suitable for solving the technological problems of a particular startup. In the logic of open-source technology, you can rank and clarify with a startup why the team chose this or that technology, find out what selection criteria were used, why they considered that the particular solution was more interesting and more modern than another, and so on. The ideal combination of circumstances is when a startup has worked through all these issues for evaluation, provided links to publications, expert opinions, the results of an internal analytical study, or confirmed that it can theoretically hire an expert who can validate all information and documents. Of course, we are not protected at the same time from fakes, we can question the authority of the expert. But if he puts his signature, then this adds more weight than some alternative technology, where it does not exist. At the same time, experts can also be mistaken or be biased and pursue some personal goals.
Let’s look at the closed technologies. As soon as it is closed, it should be protected by someone and somebody who owns it. We try to research who is the owner and clarify what are the applicability limits of this technology according to the rules. You can look at license agreements, study cases, analyze what Microsoft, Amazon or someone else who owns this technology did, for example, and accordingly compare it with similar technologies from other brands, in order to understand whether it makes sense to integrate this technology. So in this case, the confirmation is not the wisdom of the crowd (as for open-source technologies), but the brand of masters from this sphere. For example, Microsoft experts in the person of Bill Gates confirm that their cloud at Microsoft is quite safe and fast, they have marketing material demonstrating that their cloud is still working on the scale of a billion users, so the startup can connect and be sure of reliability and security of such a decision. Although in any case, we must ask the startup a question: what will it do when there will be, for example, 2 billion users? In the context of Due Diligence of technologies, it is necessary to find out whether the startup worked out this information field in principle. What will happen when it faces restrictions on existing technologies that it doesn’t own? How will he solve this problem?
How to compare technologies and mix open-source with the closed ones — it is quite a difficult question because, from the one side, many open-source licenses “spoil” the product. The assumption, that the final product is a product with an open code even when we scale it; and from the other side, it fails to satisfy the vendors’ rules of using closed technologies. For example, there may be potential risks that at some moment, Google maps will be payable, as there are more than 10000 usage requests of maps. The same can be said about how the startup develops its own technology or solution. Who can prove that this is a scalable story, it is safe and who will conduct synthetic and real tests? Potentially, it may be the biggest know-how, however, it is the riskiest and the most potentially scummed territory, when we don’t use the technology that was already discovered but reinvent it.
...

At the heart of the methodology, there is a technology life cycle. It starts with an idea and ends up with a complete technology distribution for solving a specific type of task. Usually, it happens, that there are 1–2 technologies in the industry, that may ideologically differ by the way of solving the task, and there is everything else, that takes the niche boundaries. Accordingly, it is necessary to define how the technology suits the startup, and not the technology itself but the maturity of this technology in gear with the method of solving different tasks for the startup. The core principle lays in the evaluation at each stage of elaboration of a specific issue by a startup (in the context of technology, of course).
The logic of the methodology questionnaire is simple: the expert clearly answers “yes” or “no” to the range of consistent questions about the state of startup’s technologies. If the answer is “yes” — you can move to the next question. If the answer is “no” — there is no sense to go to the next question, we focus on this specific question, defining it as the nearest development point of the project’s technological part.
If we take the example of Ms.Holmes, she would stop on the 4th step (out of 10) of my methodology, providing she didn’t have an independent expert’s report on whether her technologies can be realized, scaled, whether they are safe and truly exist in the world. Accordingly, either she would have to convey a technological audit and get the сonclusion from authorized engineers, that the technology really exists, or to prove, that the startup conducted tests and the technology actually works at a specific scale; to show the security professional’s conclusion, that all the data is stored inappropriate way.
The evaluation procedure can be described in 10 steps.
The general description of the system’s work algorithm, technology and its blocks, structure and type of data.
Providing of technical documentation and technical system requirements, describing what is taken at the start: how and where is data processed, where is it transferred and etc.
Presenting the specification — the description of how the system has to work in detail, step-by-step.
Alternatives for each system part are next to scrutinize: where and what kind of data will be stored, what are the databases, what are the provided ways of storing (personal/cloud/distributed servers on machines/computers etc.)
On the fifth step, you have to understand whether alternatives are scrutinized. If they are, then what were selection criteria and which technology did you choose to solve this specific fragment, regarding claimed requirements and observed alternatives. The startup’s task at this stage is to report about the chosen technologies. In such a way, you can already understand that there is a mobile application which is developed for some platforms with the help of specific frameworks, and the team viewed several alternatives before the development process.
On the sixth step, you have to present the expert’s conclusion, which proves the chosen technologies to be the best possible. In other words, you have to enlist the support of community, vendor or independent experts that, for example, it makes sense to store the selected data on a distributed ledger in this specific case.
At this step, there should be provided the proof, that with the help of selected technologies in claimed conditions, the task can be completely solved. In other words, if we assume that the startup is aimed at the million-strong audience, it has chosen some technological alternatives, we have to assure that it is possible to close this case with the help of chosen technologies. For example, at the scale of 100 people at a given time period, the MVP works perfectly but when the task will be to deliver the information to at least half-a-million spots, the delivery speed may become way too slow, and in these conditions, it will be impossible for the startup to solve the given task.
Further on, it is important to discuss the correspondence of the current speed measurements, the availability of resources, measurements of computation capacity to the claimed values. The task is to prove that there is not only a theoretical way to work out the task in advance but that it is possible to test on a real example, and there are actual servers, which the startup can take or buy at some price.
Only at the ninth step, we talk about security. Until we don’t have a clear vision that the technology will be large-scaled and popular, there is no point to discuss the security on purpose. For example, if we analyze the alternative, security will always be one of the criteria. When we evaluate the solution in general, the security question is discussed almost at the very end.
The last step of the evaluation proves that the chosen technology (or technologies) are de facto industrial standards for similar cases and tasks. Then a question arises — why did nobody else create this kind of a startup before? And if it happens, that the startup brings something new to other startups considering other parameters: business model, low-competitive market, and it appears that it is based on common technologies, that have proven their viability, safety, and they are commonly used in the professional area, it receives 10 points in this scale. So to say, our scale is quite broad: it starts from 1 — formalization of an idea, and to 10 — where, for instance, it is YouTube — a technology for sharing and posting video content.
Each of these steps is necessary and vital to a startup, not only to attract investments and pass successfully the Due Diligence but also for the inner technology status evaluation. To continue working and developing the technology, it has to work out a specific list of documents, approve and test a specific range of hypotheses. In this context, my methodology is some kind of evaluation criteria for technological management in the startup.
...
Let’s say, there is Kaspersky, that is an expert in cyber-security in the Russian-speaking community. We masterminded, that we will store our data in txt-files, that are ciphered by an algorithm, that will be distributed on users’ mobile devices in our system. With this, from the point of view of modern approaches, it may not be the most appropriate way. But we ask Kaspersky representatives, whether this method is safe enough so that we do not have the majority manipulations, that no one has the opportunity to decrypt, replace the data somewhere along the way, and so on. And they conclude that from this point of view this method is quite safe, they recommend it. Or they say “we do not recommend”, because (and further listing).
...
What considers financial investor, you may not struggle with getting high evaluation marks in the technical scale, it is better to focus on the marketing, distribution, market, good team, in which he will believe and invest, as he will not re-check and go into details. So there is a high chance of successfully selling this asset when the project will start to grow. So, it is enough to get 3–4 points in technology criteria, which is pretty easy, and put major efforts in other parameters. This will be a signal, that by doing so, you are building some idea, and nominally, the investor can relatively easy multiply his capital, as fast exponential growth is possible here, and for example, when a big player comes, he will just buy a startup, and change technologies. There is even statistics, that the two largest venture funds — Google and Amazon — are buying technologies, which perhaps, will never be used after.
A startup, that is aimed at the strategic investor, has to consciously search for a company, where it can become a part of a puzzle. A perfect case is when it happens through the knowledge transfer (when both the team and technology are bought) and inner technology migration. For example, a startup doesn’t have a strict method of distributing to the client. In other words, it doesn’t have a possibility to attract clients by the declared price, so the economy would converge. It understands that CAC is $100 and it is impossible to do attract new clients consequently. But if it has a competitive technology, it will be able to merge with another company, which has the same target audience with the price of $10 per user, and then the evaluation will be very good.
...
Technology can either be undervalued or overvalued but at specific milestones of its popularity. So when it is an early-hype stage, the technology is overrated. Such being the case, there is no warrant that the technology is scalable, that it is safe and works quickly, and so on, because there are very few practical cases of its implementation. There are just a few concepts that are being finalized — and that’s it. That’s why somebody may think that they found a “new feature” and will close the old needs with the new technology. And then they conceptualized it, analyzed, and quickly got 3 points. However, the next points are not to come cheap, because there is a need to confirm that the technology is proven to be viable for the next 10 years. And when the technology is young, it doesn’t have this horizon and needs some strong cases, which prove that it is going to be scalable and that the connections, that grow exponentially, don’t violate the indicators that we get, when there are not many elements.
Gartner’s Hype cycle — it is a graphic representation of the penetration, adaptation and social impact of specific technologies. This is a graph that shows public expectations from a particular technology. According to Gartner, in the perfect case, the technology successively goes through 5 stages: the launch, the peak of inflated expectations, the valley of disappointment, the slope of enlightenment, the plateau of productivity. — Startup Jedi.
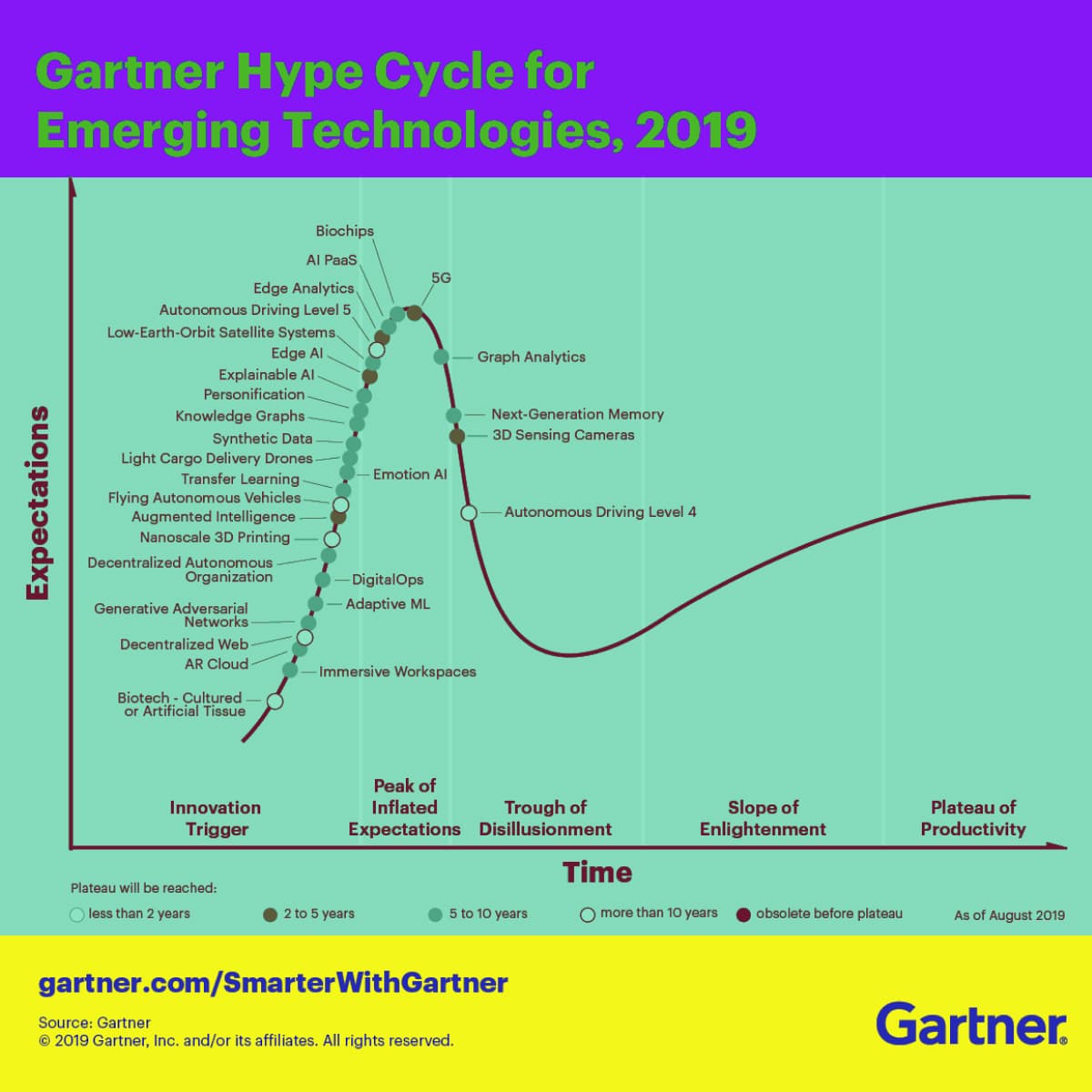
Another issue is security: when you push technology, the level of information hygiene and technical safety drops, so someone can, for example, get access to devices because some adapters are not used. At the same time, if the technology is mature and we appear after the hype period or even closer to the end of the hype, this is a good sign for a startup. Meaning that the technology, which it relies on, is already time-tested, fully confirmed of safety and scalability.
But then, another difficulty arises: how to build a business on this technology? That is, the main task is to create something new, using only time-tested and old technologies. That is the creative moment of invention. In fact, if the previous steps are elaborated, the art process by TRIZ (Theory of Inventive Problem Solving) and invention begins. Some technologies may seem boring because they are not popularly discussed anymore, too many people know about them and nobody studies anymore. But there might be something special, that appears to be a highlight. Then, this underestimated technology can be brought to the market, which it enters in a new, more powerful way.
There was a perfect question about to whom and how to sell the project. The solution may be found by answering the question: how do you plan to make money? Generate a money-flow, sell the patent, sell the team? If so, then who will you sell to and when? Depending on the answers, you have to form your further strategy. It is impossible for a startup to do everything if it plans to grow fast and exponentially.
Facebook: facebook.com/StartupJedi/
Telegram: t.me/Startup_Jedi
Twitter: twitter.com/startup_jedi
Comments